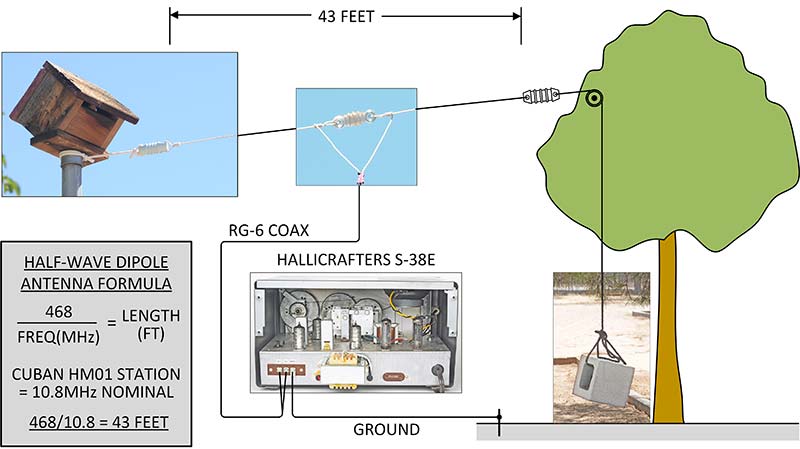
How to Hack Radio Frequencies: Building a Radio Listening Station to Decode Digital Audio & Police Dispatches « Null Byte :: WonderHowTo

Mum's horror as stranger intercepts her daughters' toy walkie talkie signals and asks where they live | The Sun

Silent Wings Museum - In-Flight Communication - Radio Radios were designed for two-way communication on a shared, precisely tuned frequency between glider and tow plane. The SCR-585-A radio was functional up to
It is possible to change the internet signal from the home router to a radio signal and send it to another walkie-talkie and by changing the radio signal again to an internet